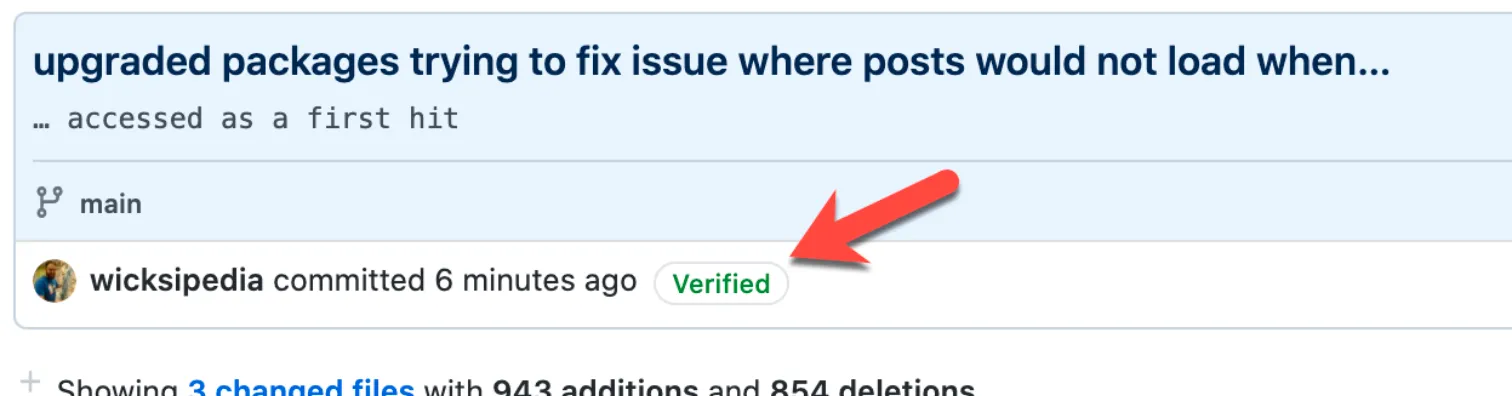
Have you ever looked a PR in GitHub and noticed that some commits have a Verified chip and some don’t? And that it’s usually the PR merges that do? What gives?
Well it turns out that you are able to sign your commits with PGP to verify that you actually committed them! It’s easy to set different details when authoring a commit:
git commit --author="Not Matt Wicks <someone.else@example.com>"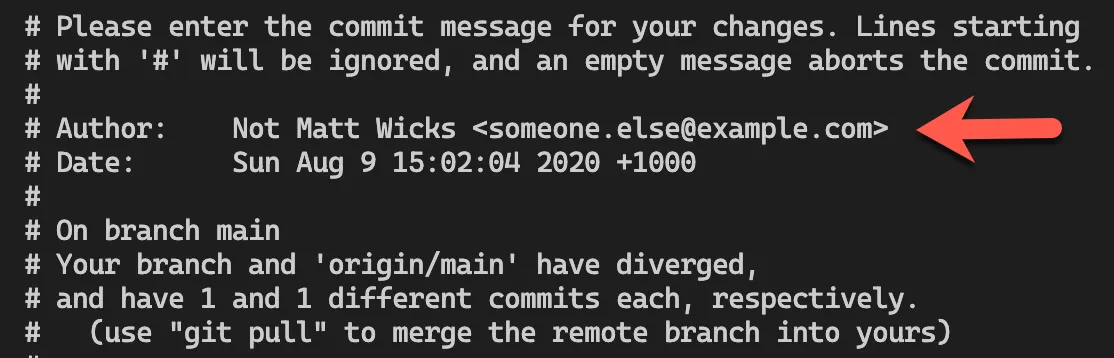
Let’s not jump to the conclusion that this is a universally bad thing - there are valid reasons when you want to commit something in someone else’s name. For example, at SSW we are migrating SSW Rules from a SharePoint site to a staticly generated site using Gatsby and GitHub. We want to preserve the history i.e. I wrote or updated a rule, then the commit message should be in my name - that way the history stays intact. Being able to set the author is critical for this to work.
Although, for my recent work - I’d like to let others know it was definitely me who committed the work (good or bad).
How I set it up
The GitHub docs were pretty good but I deviated on a couple of things:
UPDATE: 1Password now does this for me and was much easier to setup - https://developer.1password.com/docs/ssh/git-commit-signing/
(BTW I’m on a Mac, I’d love to hear how you got it to work on Windows)
Old way:
-
Install gnupg2
brew install gnupg2 brew link --overwrite gnupg -
I didn’t like the sound of GPG Suite, so I went for Pinetry for Mac to store the passphrase of the PGP key in the OS keychain
brew install pinentry-mac echo "pinentry-program /usr/local/bin/pinentry-mac" >> ~/.gnupg/gpg-agent.conf killall gpg-agent -
Now that the tools are installed, we can generate a PGP key that GitHub can use. You will need to enter your name and email address (make sure they match the ones used in your Git config - don’t ask why I know 😉)
gpg --default-new-key-algo rsa4096 --gen-key -
You’ll need a passphrase for the PGP key - I recommend using a password manager to generate and store (I use 1Password)
-
Let’s grab the secret’s key In the GitHub example: 4096R/3AA5C34371567BD2 we can see that:
- it’s using 4096bit RSA
- the key is 3AA5C34371567BD2
$ gpg --list-secret-keys --keyid-format LONG /Users/hubot/.gnupg/secring.gpg ------------------------------------ sec 4096R/3AA5C34371567BD2 2016-03-10 [expires: 2017-03-10] uid Hubot ssb 4096R/42B317FD4BA89E7A 2016-03-10 -
Export and copy the key (make sure to include the -----BEGIN PGP PUBLIC KEY BLOCK----- and -----END PGP PUBLIC KEY BLOCK-----)
gpg --armor --export 3AA5C34371567BD2 -
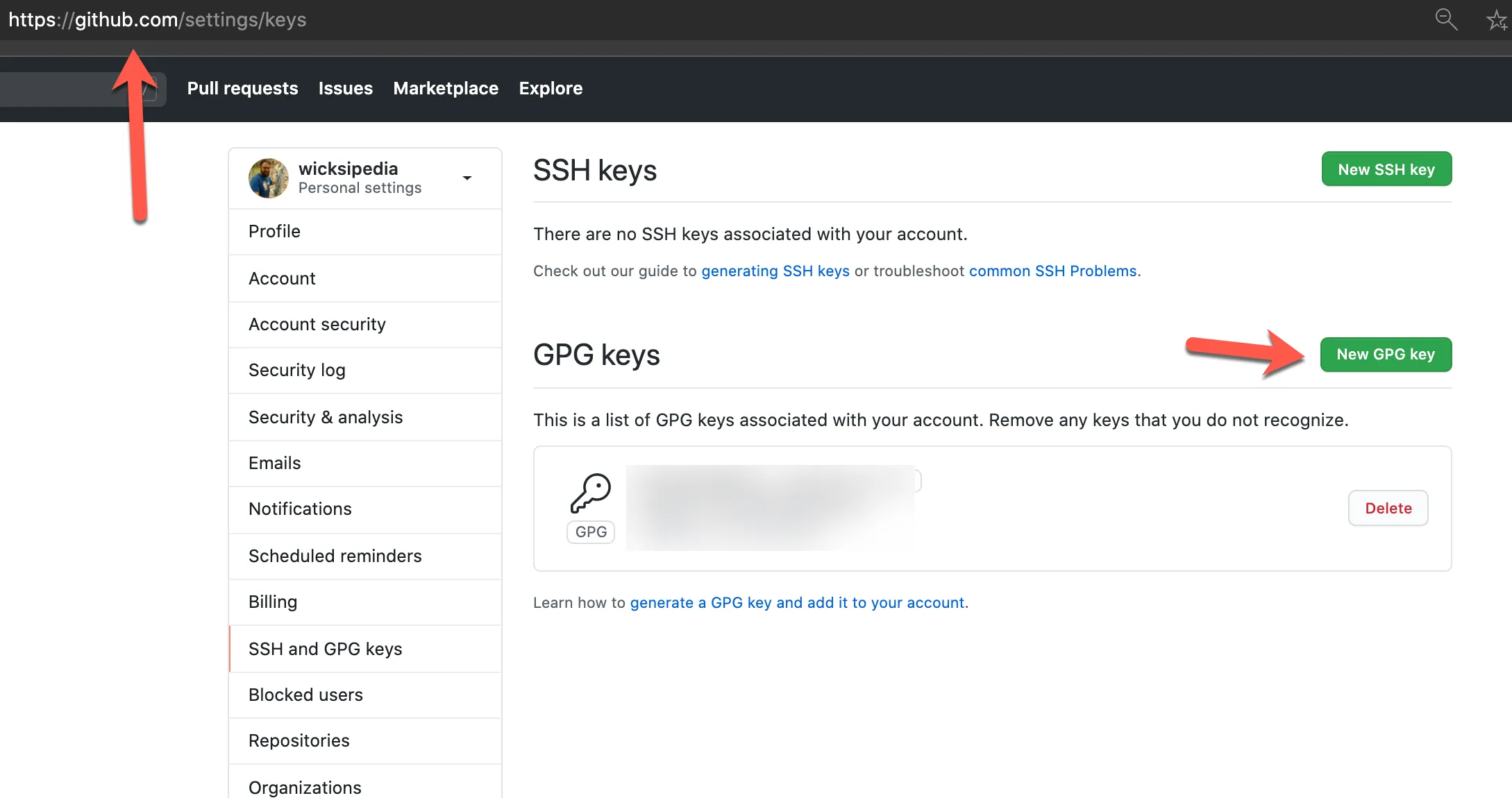
Go to Github - SSH and GPG Keys and
- Click New GPG Key
- Paste the key in the textbox
- Click Add GPG Key
-
Now let’s tell Git to sign commits and which PGP key to use
git config --global user.signingkey 3AA5C34371567BD2 git config --global commit.gpgsign true -
You’re done! Commit and push your signed commits!
Once you’ve got commit signing set up, you can take your GitHub workflow to the next level by managing repository settings as code, which makes branch protection and other repo configurations as trackable as your commits.
Hope this helps! Let me know how it goes!